
There is a Hacker News article that came out a couple months ago that recently resurfaced and started making the rounds in TUNE’s Slack channels. The article states that McAfee researchers found four imposter extensions for Google’s Chrome browser had generated 1.4 million installs. The malicious extensions were rather unrelated in nature, being two Netflix group watching extensions, a coupon extension, and a website screenshot extension. But they all had one thing in common: They were tracking the website activity of users and injecting malicious code, a fraudulent practice known as cookie stuffing, in order to profit from retail affiliate programs.
But the story didn’t have to end that way for those retail brands. If they had been using TUNE, this might not be a story at all. Here’s why.
How Cookie Stuffing Works
Cookie stuffing is a type of ad fraud that’s all too common today. Cookie stuffing occurs when fraudsters — in this case, malicious extensions masquerading as legitimate ones — generate clicks for affiliate programs without having an actual human being click on anything. The user, who has downloaded the fake extension thinking they have the real deal, has zero knowledge of being used in this ploy.
When the user visits a website, a tracking session is started; if they eventually purchase a product, the extension claims credit for the conversion and gets a commission for the purchase, even though it had nothing to do with the consumer finding and buying that product. The retail brand running the affiliate program is unaware they are paying out for fraudulent activity, since the extension is disguising itself as a legitimate publisher in the program. Usually, this type of fraud targets the affiliate programs of large, popular brands, as there is a better chance for a higher volume of people to convert.
How to Flip the Script
One way to combat this style of cookie stuffing is to have strict partner management and vetting practices. These practices should require affiliates to be transparent about their placements and how they drive traffic. They should also include constant audits to ensure quality, even when the quality looks good on paper.
All of these controls, plus many more, are available in the TUNE Partner Marketing Platform.
Fight Fraud with Time-to-Action Tools
In addition, TUNE also offers Time-to-Action rules and reports that can help notify brands of suspicious conversion patterns in their traffic. In this scenario, where fraudsters are waiting until a user gets to your website before firing fake clicks, you can set various thresholds to alert you if traffic volume is performing out of scope when it comes to the amount of time it takes from a click to a purchase.
Here’s a step-by-step example of how you could use TUNE’s time-to-action tools to identify and prevent this type of fraud.
- Look at the Time-to-Action Report in TUNE to determine your average time-to-action, or how long it takes a user to convert (e.g., purchase a product) after an affiliate link has been clicked. You may want to exclude certain partners from this analysis depending on the composition of your program.
- If you have a small number of trusted cashback or coupon partners, it’s a good idea to exclude them here, as they could skew the average time it takes to convert.
- It’s helpful to compare your affiliate traffic versus other forms of paid media to get a clearer picture of your users’ traffic patterns. Users coming from fraudsters like malicious extensions will not interact with your site in a manner consistent with affiliate traffic, as the “click” that sent them to you does not originate from a valid affiliate partner.
- Once you have your average time-to-action, expand the time range until it includes 50% of your conversions (sales, registrations, etc.).
- Example: If your average time-to-action is 25 minutes, start widening the time range until it covers half of all conversions. Let’s say that is 15 minutes to 1 hour and 30 minutes.
- Set your Time-to-Action threshold in TUNE to notify your partner manager if any affiliate has more than 50% of their traffic that converts outside of the 15 minute to 1 hour and 30 minute threshold. You can now spend some time digging into the traffic patterns and working with your partner to determine the true quality of this traffic.
- Set your Time-to-Action threshold in TUNE to block partner traffic when more than 75% of their traffic converts outside of the same 15 minute to 1 hour and 30 minute threshold.
- Traffic will be blocked and both your partner and partner manager will be notified.
- You can also block, or be notified of, traffic down to the sub-source level, so you don’t have to block traffic at the overall partner level.
Now you have some thresholds in place to combat fraudsters using this method of cookie stuffing.
Visualize Data to Identify Suspicious Activity
Another way to leverage TUNE’s time-to-action functionality for similar fraudulent activities is to translate visual data. A close cousin of cookie stuffing is the practice of starting a tracking session at any point in time, as opposed to starting it when a user goes to the intended website. This can be done in the form of pop-unders (where the user may eventually realize they have been redirected to the brand’s site, but most likely won’t notice for a while), or via server-side clicks, or clicks that do not technically send the user anywhere, but still start a tracking session. You can use TUNE’s visual reporting to see evidence of these practices.
Below is a view of a normal Time-to-Action curve. It looks much like a bell curve and shows that the natural intent of this traffic is to convert between X-X minutes.
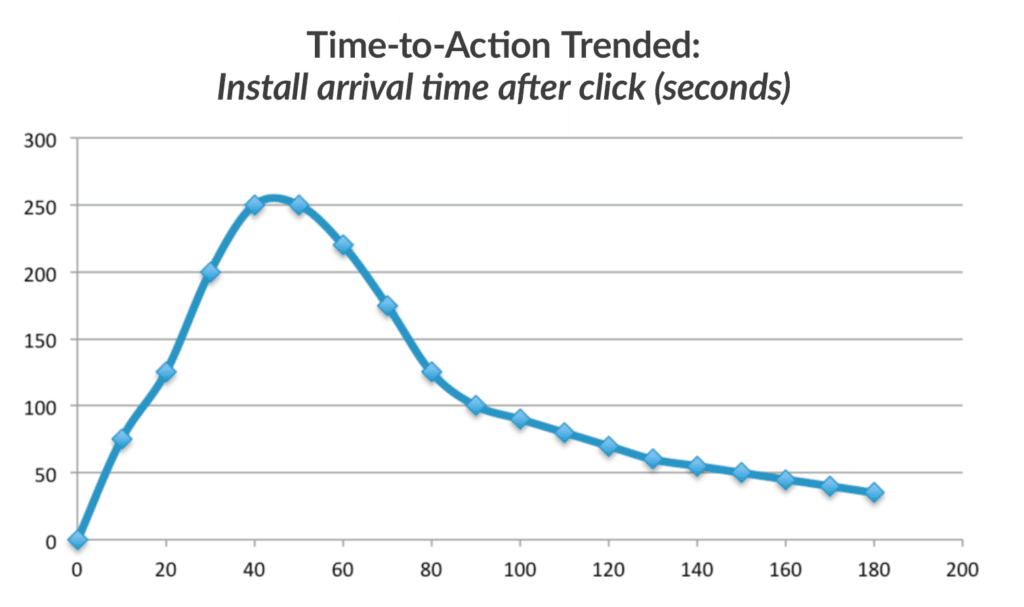
This means that users who are interacting with these partner links are most likely finding value in the content presented and then having some reasonable probability of converting.
Here we have another example of a Time-To-Action curve, but one that has no obvious intent curve. The flatter the curve, the more concerning the traffic may be.
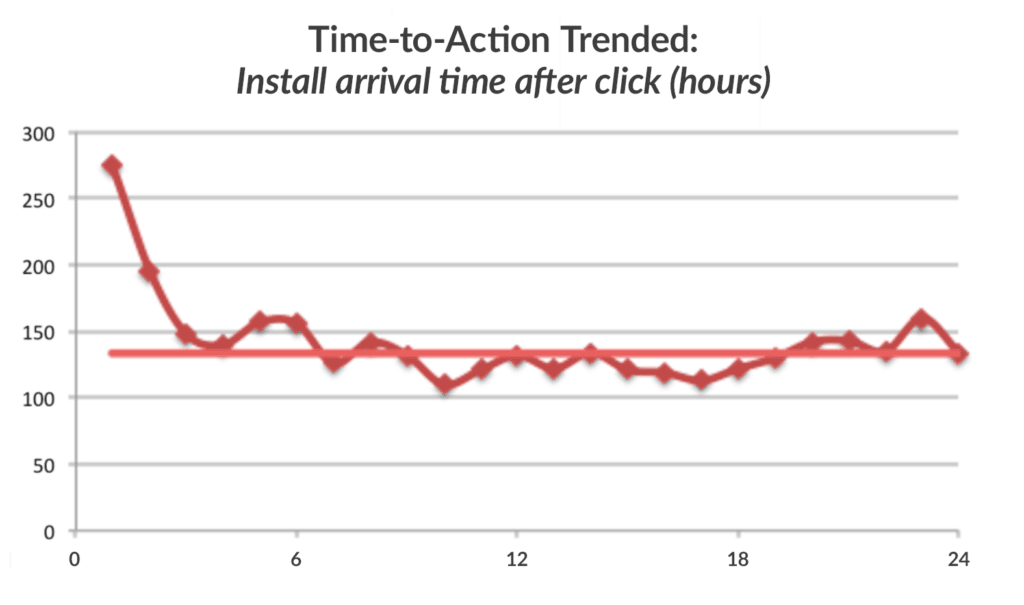
It’s obvious that one of a few scenarios is happening: either users are confused with what is being promoted via the links, they are being marketed something that is not appearing as genuine on the brand’s site (for example, offering a 50% discount when none is available), or there is something malicious going on (like the pop-unders or server-side clicks we previously mentioned).
Protect Your Program with TUNE
Situations like this one don’t have to spell doom for a program. With the TUNE Partner Marketing Platform, you can safeguard your investments against bad actors using the tools we covered above. But these aren’t the only features and functionality we offer to help combat fraudulent activity. If you’d like to hear about the rest of them, drop us a line at [email protected] or request a demo today.
Author
During his time as VP, Business Development at TUNE, Nate spearheaded the Affiliate Rockstars series, which aims to highlight the hard-working individuals in the industry and share their expertise with a wider audience. Nate received his BA in Social Sciences from Washington State University.




Leave a Reply
You must be logged in to post a comment.