
Welcome to the second installment of the TUNE Fraud Series, articles and insights from TUNE designed to make fraud actionable. Today we do a deep dive on click fraud, characterized by a fake click and a genuine user for a cost-per-install (CPI) campaign. For an introduction to fraud and the series, head over to the first article, Types of Mobile Advertising Fraud.
This is the first part of a two-part series to start the discussion around click fraud, today talking about the techniques and impact, with the following article around identification and elimination.
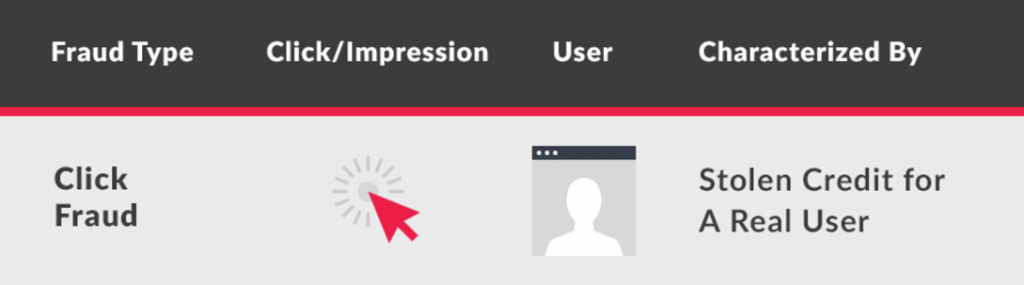
A red arrow indicates a fake click/impression, and a gray user indicates a real one.
Click Fraud Deep Dive
Click fraud recap: Click fraud occurs when clicks are simulated on a real user’s device, even though the ad was not displayed or clicked on. This is a high-return opportunity because it only requires one faked action — the click. Marketers with a large volume of organic users can be especially susceptible.

When a fraudster simulates a click on a genuine user’s device, the fraudster takes the credit whenever the user installs the app on their own. Since the user is a real human with genuine interest in the app, they behave like the typical organic user and don’t raise a red flag. (For details and examples, see Types of Mobile Advertising Fraud.)
Note that some of the impact discussions here are in the context of performance marketing where payment is based on cost-per-install (CPI). Issues with cost-per-click (CPC) campaigns exist but typically have even more challenges with fraud than performance marketing.
Impact of Click Fraud
Click fraud represents a huge opportunity for fraudsters and is becoming a destabilizing force in the industry. Anecdotally, there are marketers who have evidence that click fraud is nearing the 50% mark of their paid campaigns, and other marketers whose black-list of publishers not to work with covers over 50% of the 50 most common publishers.
There is a boxing analogy for this elevated fraud level:
- The fraud is coming in too fast to block, i.e. the boxer is outmatched.
- If the marketer has a chance to go on the offensive and fix fraud, a fraudulent publisher can introduce delaying tactics to require more and more proof before acting. This is akin to the rope-a-dope (Muhammad Ali) strategy, where one contender lets the opponent fatigue themselves while staying in a defensive posture.
Most publishers have good intentions and are not bad actors with malicious intent. In spite of the statistics above, the most common use cases found are publishers/networks that generate 95% or more good-quality traffic, with the occasional sub-publisher or country with issues. Identification and elimination of bad traffic sources in these cases can be positive for both sides.
Actors/Systems With Click Fraud
A quick discussion around the actors involved in click fraud. This type of fraud is characterized by:
- Faked click non-human actor, non-human system
- Real install human actor, human system
When the human actor did “click-with-intent,” then we have advertising at work. As we walk through the click fraud use cases, there will be a variety of techniques discussed on how the click is faked, but in all these cases the human actor did not “click-with-intent-to-install.”
The faked click (non-human actor) could actually be simulated directly on your device, compounding the ability to find the issue, since the device itself is owned and operated by a human.
Note that the non-human actor generating the faked click can’t actually predict when the human will install (different systems), but instead relies on statistical or other methods to claim the install. Since the non-human actor has no control over the timing of the human install, the time-to-install patterns appear distinctly different for non-human traffic versus human traffic. These pattern deviations are clear indicators of one or more fraud issues.
Lies, Clicks, and Statistics: Spamming Impact on Brand
Click stuffing and click spamming are common names for a variety of techniques that generate high volumes of clicks that prey on other paid installs, as well as organic installs. The faked click could be coming from malware running directly on the device, malware on a website that is visited by the device, or even generated by a bot that has captured your device information and then uses it to replay clicks.
- Malware on the device
- Malware with a mobile experience (video, mobile web game, survey, or other)
- Bot-generated clicks
Key takeaway: What is missing in all of these use cases is “click-with-intent-to-install.”
Implementation of click fraud can be as simple as generating clicks for the top social apps, top games, top ride-share apps, top reservations system apps, and then replaying those on a daily or hourly basis. When the download happens organically, attribution credit is inappropriately applied to these campaigns. For users who have interacted legitimately with paid campaigns, when the spammed click happens between real click and installation, the spammed click will get credit.
Key takeaway: Spamming can steal credit for both organic and paid installs.
Let’s walk through some scenarios to understand their impact:
1. Organic traffic + one fraudulent publisher/network
- In this scenario, the users delivered by the fraudulent campaign are real users. Methods that look for ROI (return on investment) or ROAS (return on ad spend) will show positive results for the fraudulent campaign.
- However, the fraudulent campaign will fail to deliver incrementally. The net user install rate is unchanged by the fraudulent campaign.
2. Organic traffic + one fraudulent publisher/network + one effective publisher/network
- The fraudulent campaign still shows ROAS. Fraudulent campaign lacks incrementality.
- The effective campaign will have installs stolen by the fraudulent campaign and appear as less effective than when run in isolation.
- The effective campaign is faced with pricing challenges as costs rise (ad impact stolen) and revenues decrease (attribution stolen).
- The fraudulent campaign costs may be minimal (no costs to place ads) and ability to claim installs from other sources may be large.
Key takeaway: Engagement with a click spamming provider breaks your ability as a marketer to evaluate other publishers/networks.
Ad Stacking, Hidden Ads, and Impressions Labeled as Clicks
There are a variety of click fraud techniques that do not involve a device compromised by malware but passively misrepresent or over-represent click activity upon visiting a site hosting an ad.
The actual implementation details don’t especially matter; the user visits a site, and the site represents that the user clicked on one, 10, or 100 ads. The ads could be visible or not visible, clicked on or not clicked on, seen for long periods or just flashed once. There could be one, 10, or more.
The core issue is unchanged from other spamming techniques:
Key takeaway: What is missing in all of these use cases is “click-with-intent-to-install.”
Impact matches the other spamming techniques as well:
Key takeaway: Engagement with an ad stacking, hidden ads, impressions-as-clicks provider breaks your ability as a marketer to evaluate other publishers/networks.
Click Injection
Click injection is a technique typically, but not exclusively, occurring on Android devices whereby malware uses polling and broadcast techniques to identify that a download for an app has initiated. The malware then initiates a click event to take credit for the installation before the app is opened for the first time.
The sequence of events follows a couple basic timelines:
Organic install starts
> malware detects and fires click
> install completes and attribution is determined
Paid campaign install starts
> malware detects and fires click
> install completes and attribution is determined
Additional details on some of the malware can be found by searching for keywords Hummingbad, Hummingwhale, Skinner, or Chamois (although the list continues to grow). Credit to Check Point Software Technologies (among others) for identification of some of the specific malware.
The core issue is the same, but the impact is larger:
Key takeaway: Click injection will steal credit from both organic and paid, but can happen for every install on that device.
Click injection impact when measured in isolation is similar to other techniques:
1. Organic traffic + one fraudulent publisher/network
- In this scenario, the users delivered by the fraudulent campaign are real users. Methods that look for ROI or ROAS will show positive results for the fraudulent campaign.
- However, the fraudulent campaign will fail to deliver incrementally. The net user install rate is unchanged by the fraudulent campaign.
2. Organic traffic + one fraudulent publisher/network + one effective publisher/network
- Fraudulent campaign still shows ROAS. Fraudulent campaign lacks incrementality.
- The effective campaign has far more installs stolen by the fraudulent campaign and may appear to be completely ineffective.
- Effective campaign may incorrectly show negative ROAS.
- The fraudulent campaign will appear as both cheaper and more effective than the real campaign.
Impact matches the other spamming techniques as well:
Key takeaway: Engagement with a click-injection publisher/network breaks your ability as a marketer to evaluate other publishers/networks.
Closing Remarks
Elimination of fraudulent traffic sources is important when allocating marketing budgets to avoid bad publishers/networks. However, the largest impact from even one fraudulent traffic source is that it breaks your ability to properly measure the effectiveness of your other campaigns (although multi-touch would enable looking past the last click to understand attribution).
Key takeaway: The fraudulent publishers/networks can, in many cases, come in as both cheaper and with a greater ability to drive installs.
At TUNE we talk about the “Lean Marketer,” leveraging the learnings from the “The Lean Startup” by Eric Ries to enable a model where our Marketers can:
Measure Faster > Learn Faster > Change Faster
Click fraud breaks the ability to implement this model, clouding all measurements.
Fortunately, there are characteristics of all of these spamming techniques that can identify the portion(s) of the traffic that are fraudulent. In all of these click-fraud use cases there are very clear patterns that demonstrate a clean break from normal human behavior. These can be used to measure, identify, and remove the bad traffic sources quickly.
Ready for the next post in the TUNE Fraud Series? Head over to Mobile Click Fraud Search and Destroy to learn how to find and eliminate these click-fraud techniques.
Download our report, “Mobile ad fraud: what 24 billion clicks on 700 ad networks reveal,” to learn more about fraud, or read the blog post for key highlights.
Author
Becky is the Senior Content Marketing Manager at TUNE. Before TUNE, she handled content strategy and marketing communications at several tech startups in the Bay Area. Becky received her bachelor's degree in English from Wake Forest University. After a decade in San Francisco and Seattle, she has returned home to Charleston, SC, where you can find her strolling through Hampton Park with her pup and enjoying the simple things in life.



Leave a Reply
You must be logged in to post a comment.